"Unable to open a session" - unable login to centos server from ezeelogin jump server
Unable to open a session- ssh session fails with pam_systemd(sshd:session): Failed to create session
Overview: This article provides troubleshooting steps to resolve the "Unable to open a session" error that occurs when logging into the remote server via Ezeelogin gateway. It includes steps for verifying SSH connectivity, adjusting timeouts, restarting systemd-logind.service, and managing /var/log/btmp size to ensure reliable authentication and session management.
Sep 4 17:56:05 server2 crond[938922]: pam_systemd(crond:session): Failed to create session: Activation of org.freedesktop.login1 timed out
Sep 4 17:56:05 server2 sshd[938752]: pam_systemd(sshd:session): Failed to create session: Activation of org.freedesktop.login1 timed out
Sep 4 17:56:05 server12 sshd[938752]: pam_unix(sshd:session): session opened for user root by (uid=0)
Sep 4 17:56:05 server12 sshd[938752]: debug1: rekey after 4294967296 blocks
Sep 4 17:56:05 server12 sshd[938752]: debug1: rekey after 4294967296 blocks
Sep 4 17:56:05 server12 sshd[938752]: debug1: ssh_packet_set_postauth: called
Sep 4 17:56:05 server12 sshd[938752]: debug1: Entering interactive session for SSH2.
Sep 4 17:56:05 server12 sshd[938752]: debug1: server_init_dispatch
Sep 4 17:56:05 server12 sshd[938752]: debug1: server_input_channel_open: ctype session rchan 0 win 2097152 max 32768
Sep 4 17:56:05 server12 sshd[938752]: debug1: input_session_request
Sep 4 17:56:05 server12 sshd[938752]: debug1: channel 0: new [server-session]
Sep 4 17:56:05 server12 sshd[938752]: debug1: session_new: session 0
Sep 4 17:56:05 server12 sshd[938752]: debug1: session_open: channel 0
Sep 4 17:56:05 server12 sshd[938752]: debug1: session_open: session 0: link with channel 0
Sep 4 17:56:05 server12 sshd[938752]: debug1: server_input_channel_open: confirm session
Sep 4 17:56:05 server12 sshd[938752]: debug1: server_input_global_request: rtype [email protected] want_reply 1
Sep 4 17:56:05 server12 sshd[938752]: Received disconnect from 112.227.16.12 port 49315:11: Channel failed
Sep 4 17:56:05 server12 sshd[938752]: Disconnected from 112.227.16.12 port 49315
Sep 4 17:56:05 server12 sshd[938752]: debug1: do_cleanup
Sep 4 17:56:05 server12 sshd[938752]: debug1: PAM: cleanup
Sep 4 17:56:05 server12 sshd[938752]: debug1: PAM: closing session
Sep 4 17:56:05 server12 sshd[938752]: pam_unix(sshd:session): session closed for
Step 1: Ensure that you can manually SSH from the gateway server to the remote server ( bypassing the Ezeelogin ezsh interface).
root@gateway:~# ssh username@remoteserver_ip or hostname
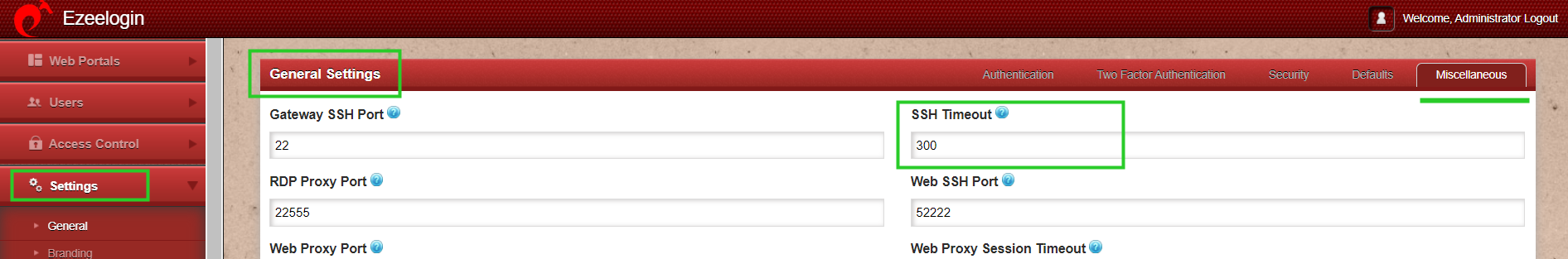
Step 2: Change the SSH Timeout value to 300 seconds from 10 seconds to rule out network slowness and a connectivity issue. Navigate to Settings -> General -> Miscellaneous -> SSH Timeout
Step 3: Restart systemd-logind.service on the remote server:
root@remoteserver:~# systemctl restart systemd-logind.service
Authentication by SSH key DB failed :
Channel failed (shell): Timed out waiting on socket
Step 5: Check for the messages under /var/log/secure and /var/log/messages
sshd[236622]: Accepted publickey for root from 46.232.178.114 port 40506 ssh2: RSA SHA256:cpVnOWHn+WeiGl4JuYAlMtx39Vx5Dz82CuN7I12yITI
sshd[236622]: pam_unix(sshd:session): session opened for user root by (uid=0)
systemd-logind: New session c100 of user root.
systemd: Started Session c100 of user root.
systemd-logind: Removed session c100.
root@remoteserver:~# ls -lah /var/log/btmp
Step 7: If the size of /var/log/btmp is high then truncate the logs in /var/log/btmp. You can truncate the logs by running the following command on the remote server.
root@remoteserver:~# > /var/log/btmp
Related Articles:
Unable to ssh / An error occurred. Please contact the administrator.
unable to SSH because ip is not allowed because none of the user’s groups are listed in AllowGroups.