How to create filters in Ezeelogin while using LDAP or AD authentication?
How to create filters in Ezeelogin while using LDAP or Active Directory (AD) authentication? / Does Ezeelogin allow user authentication based on AD or LDAP groups?
Overview: The article explains how to add filters to Ezeelogin by editing LDAP or AD settings to manage user authentication based on group memberships. It includes examples of using ldapsearch commands to verify user membership within specific groups and demonstrates how to create filters with multiple conditions using operators like & and |. This ensures that Ezeelogin can authenticate users based on group memberships effectively.
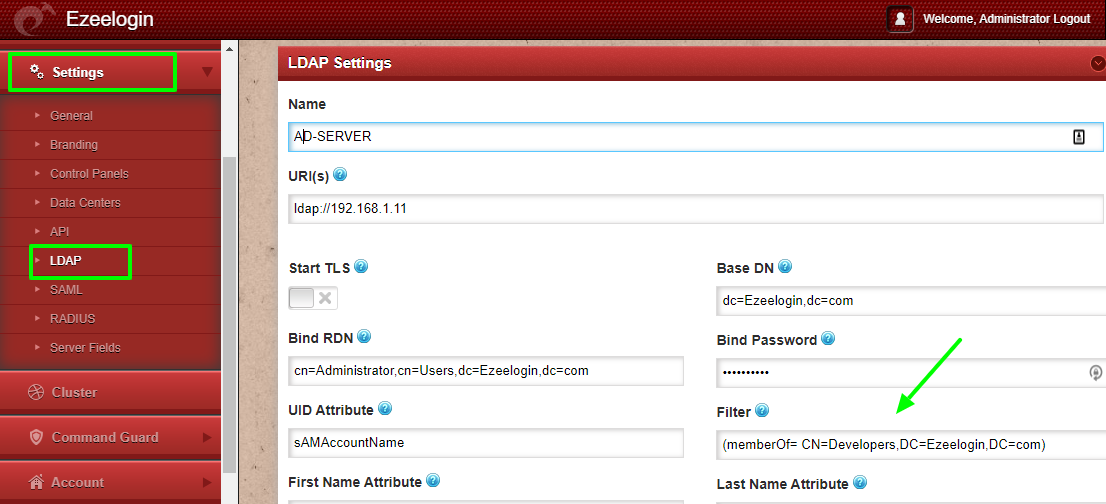
You can add the filter in Ezeelogin by editing the LDAP or AD configuration under Settings >> LDAP . The following image shows the LDAP configuration page with a sample filter matching the user's inside the " Developers "group.
root@gateway:# ldapsearch -x -b " Base DN " -H ldap_host_IP -D " Bind RDN " -W "(ldap_filter)"
root@gateway :# ldapsearch -x -b "dc=Ezeelogin,dc=com" -H ldap://192.168.1.11 -D "cn=Administrator,cn=Users,dc=Ezeelogin,dc=com" -W "(memberOf= CN=Developers,DC=Ezeelogin,DC=com)"
Enter LDAP Password:
# extended LDIF
#
# LDAPv3
# base <dc=Ezeelogin,dc=com> with scope subtree
# filter: (memberOf= CN=Developers,DC=Ezeelogin,DC=com)
# requesting: ALL
#
# rini PF., Ezeelogin.com
dn: CN=rini PF.,DC=Ezeelogin,DC=com
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: rini PF.
givenName: rini
initials: PF
distinguishedName: CN=rini PF.,DC=Ezeelogin,DC=com
instanceType: 4
whenCreated: 20210127203733.0Z
whenChanged: 20210309201301.0Z
displayName: rini PF.
uSNCreated: 12754
memberOf: CN=Developers,DC=Ezeelogin,DC=com
memberOf: CN=Eztest,DC=Ezeelogin,DC=com
uSNChanged: 53323
name: rini PF.
objectGUID:: VmjHdiz8qEagbd4Zc9H+2A==
userAccountControl: 512
badPwdCount: 0
codePage: 0
countryCode: 0
badPasswordTime: 132562563956027090
lastLogoff: 0
lastLogon: 132562564935720206
pwdLastSet: 132562564801090925
primaryGroupID: 513
objectSid:: AQUAAAAAAAUVAAAAxviuHtZf2ydRMK4HUAQAAA==
accountExpires: 9223372036854775807
logonCount: 0
sAMAccountName: rini
sAMAccountType: 805306368
userPrincipalName: [email protected]
objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=Ezeelogin,DC=com
dSCorePropagationData: 20210309201301.0Z
dSCorePropagationData: 16010101000000.0Z
lastLogonTimestamp: 132562564935720206
# Irin Mathew, Ezeelogin.com
dn: CN=Irin Mathew,DC=Ezeelogin,DC=com
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: Irin Mathew
sn: Mathew
givenName: Irin
distinguishedName: CN=Irin Mathew,DC=Ezeelogin,DC=com
instanceType: 4
whenCreated: 20210305025714.0Z
whenChanged: 20210309201324.0Z
displayName: Irin Mathew
uSNCreated: 41011
memberOf: CN=Sysadmins,DC=Ezeelogin,DC=com
memberOf: CN=Developers,DC=Ezeelogin,DC=com
memberOf: CN=centosuser,DC=Ezeelogin,DC=com
memberOf: CN=Eztest,DC=Ezeelogin,DC=com
uSNChanged: 53325
name: Irin Mathew
objectGUID:: /FxMlRFpP02h3MkM572bdg==
userAccountControl: 66048
badPwdCount: 0
codePage: 0
countryCode: 0
badPasswordTime: 0
lastLogoff: 0
lastLogon: 0
pwdLastSet: 132593866344903752
primaryGroupID: 513
objectSid:: AQUAAAAAAAUVAAAAxviuHtZf2ydRMK4HVgQAAA==
accountExpires: 9223372036854775807
logonCount: 0
sAMAccountName: irin
sAMAccountType: 805306368
userPrincipalName: [email protected]
objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=Ezeelogin,DC=com
dSCorePropagationData: 20210309201325.0Z
dSCorePropagationData: 20210305030624.0Z
dSCorePropagationData: 20210305025714.0Z
dSCorePropagationData: 16010101000000.0Z
Note: After saving the filter, click on the User>> LDAP tab to list the users under the LDAP group.
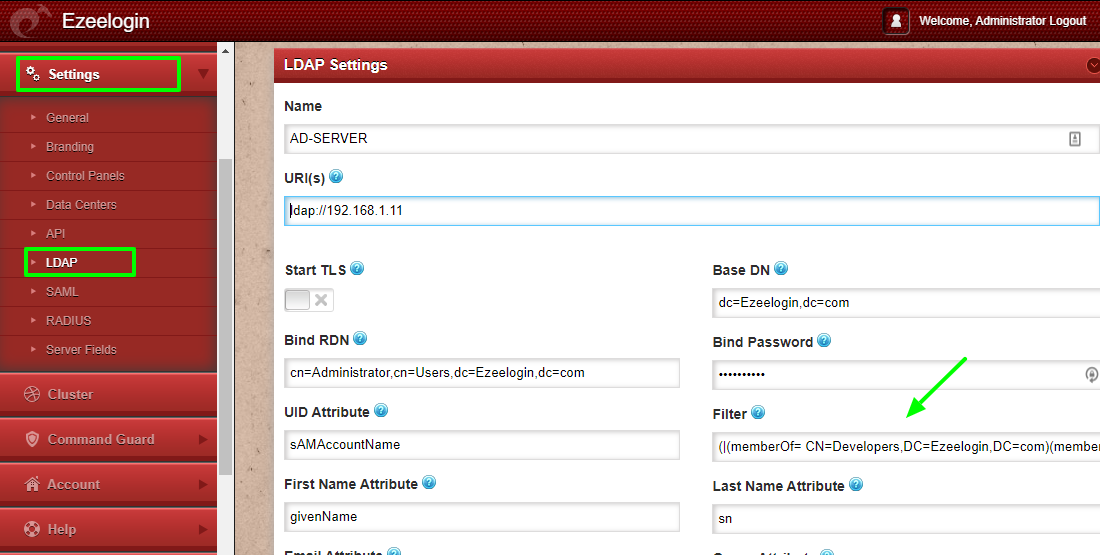
How to create a filter with more than one condition?
We can create filters with more than one condition by using certain operators like & , | , etc. For example, create a filter to list the users that are common in " Developers " and " Sysadmins " where Irin is a common user.
The syntax for the filter with the operators is as follows.
root@gateway:# ldapsearch -x -b " Base DN " -H ldap_host_IP -D " Bind RDN " -W "(operator(filter_1)(filter_2)(filter_n))
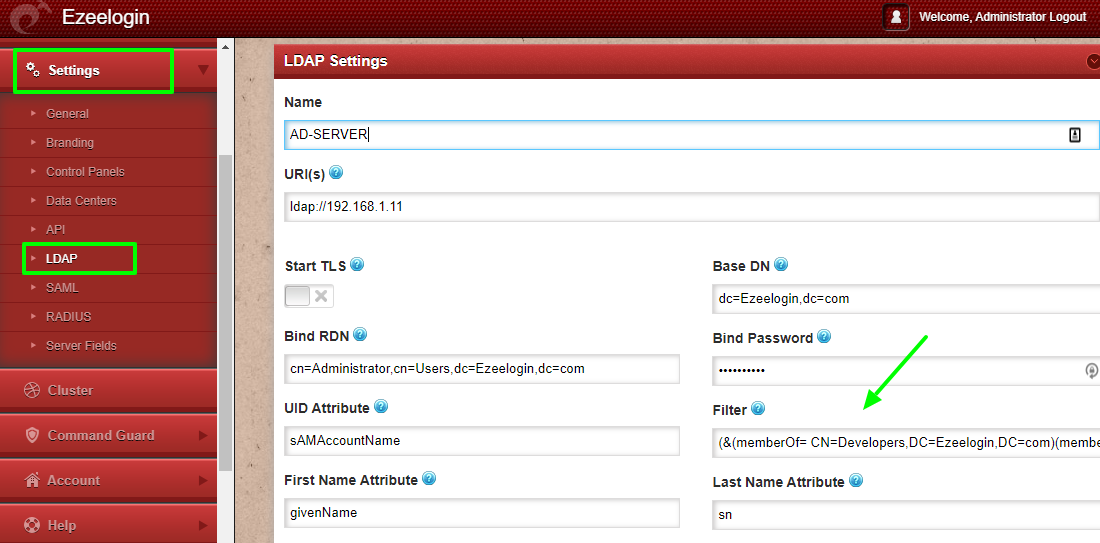
Given below is the LDAP search for the above filter.
root@gateway:# ldapsearch -x -b "dc=Ezeelogin,dc=com" -H ldap://192.168.1.11 -D "cn=Administrator,cn=Users,dc=
Ezeelogin,dc=com" -W "(&(memberOf= CN=Developers,DC=Ezeelogin,DC=com)(memberOf= CN=Sysadmins,DC=Ezeelogin,DC=com))"
Enter LDAP Password:
# extended LDIF
#
# LDAPv3
# base <dc=Ezeelogin,dc=com> with scope subtree
# filter: (&(memberOf= CN=Developers,DC=Ezeelogin,DC=com)(memberOf= CN=Sysadmins,DC=Ezeelogin,DC=com))
# requesting: ALL
#
# Irin Mathew, Ezeelogin.com
dn: CN=Irin Mathew,DC=Ezeelogin,DC=com
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: Irin Mathew
sn: Mathew
givenName: Irin
distinguishedName: CN=Irin Mathew,DC=Ezeelogin,DC=com
instanceType: 4
whenCreated: 20210305025714.0Z
whenChanged: 20210309201324.0Z
displayName: Irin Mathew
uSNCreated: 41011
memberOf: CN=Sysadmins,DC=Ezeelogin,DC=com
memberOf: CN=Developers,DC=Ezeelogin,DC=com
memberOf: CN=centosuser,DC=Ezeelogin,DC=com
memberOf: CN=Eztest,DC=Ezeelogin,DC=com
uSNChanged: 53325
name: Irin Mathew
objectGUID:: /FxMlRFpP02h3MkM572bdg==
userAccountControl: 66048
badPwdCount: 0
codePage: 0
countryCode: 0
badPasswordTime: 0
lastLogoff: 0
lastLogon: 0
pwdLastSet: 132593866344903752
primaryGroupID: 513
objectSid:: AQUAAAAAAAUVAAAAxviuHtZf2ydRMK4HVgQAAA==
accountExpires: 9223372036854775807
logonCount: 0
sAMAccountName: irin
sAMAccountType: 805306368
userPrincipalName: [email protected]
objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=Ezeelogin,DC=com
dSCorePropagationData: 20210309201325.0Z
dSCorePropagationData: 20210305030624.0Z
dSCorePropagationData: 20210305025714.0Z
dSCorePropagationData: 16010101000000.0Z
root@gateway:# ldapsearch -x -b "dc=Ezeelogin,dc=com" -H ldap://192.168.1.11 -D "cn=Administrator,cn=Users,dc=Ezeelogin,dc=com" -W "(|(memberOf= CN=Developers,DC=Ezeelogin,DC=com)(memberOf= CN=Sysadmins,DC=Ezeelogin,DC=com))"
Enter LDAP Password:
# extended LDIF
#
# LDAPv3
# base <dc=Ezeelogin,dc=com> with scope subtree
# filter: (|(memberOf= CN=Developers,DC=Ezeelogin,DC=com)(memberOf= CN=Sysadmins,DC=Ezeelogin,DC=com))
# requesting: ALL
#
# roma Ali., Ezeelogin.com
dn: CN=roma Ali.,DC=Ezeelogin,DC=com
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: roma Ali.
givenName: roma
initials: Ali
distinguishedName: CN=roma Ali.,DC=Ezeelogin,DC=com
instanceType: 4
whenCreated: 20210127210658.0Z
whenChanged: 20210309201314.0Z
displayName: roma Ali.
uSNCreated: 12775
memberOf: CN=Sysadmins,DC=Ezeelogin,DC=com
memberOf: CN=centosuser,DC=Ezeelogin,DC=com
memberOf: CN=Eztest,DC=Ezeelogin,DC=com
uSNChanged: 53324
name: roma Ali.
objectGUID:: hxJd7NT4vkaTp+gwmJfThw==
userAccountControl: 512
badPwdCount: 0
codePage: 0
countryCode: 0
badPasswordTime: 0
lastLogoff: 0
lastLogon: 0
pwdLastSet: 132562552180870397
primaryGroupID: 513
objectSid:: AQUAAAAAAAUVAAAAxviuHtZf2ydRMK4HUgQAAA==
accountExpires: 9223372036854775807
logonCount: 0
sAMAccountName: roma
sAMAccountType: 805306368
userPrincipalName: [email protected]
objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=Ezeelogin,DC=com
dSCorePropagationData: 20210309201314.0Z
dSCorePropagationData: 20210305030609.0Z
dSCorePropagationData: 16010101000000.0Z
# Irin Mathew, Ezeelogin.com
dn: CN=Irin Mathew,DC=Ezeelogin,DC=com
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: Irin Mathew
sn: Mathew
givenName: Irin
distinguishedName: CN=Irin Mathew,DC=Ezeelogin,DC=com
instanceType: 4
whenCreated: 20210305025714.0Z
whenChanged: 20210309201324.0Z
displayName: Irin Mathew
uSNCreated: 41011
memberOf: CN=Sysadmins,DC=Ezeelogin,DC=com
memberOf: CN=Developers,DC=Ezeelogin,DC=com
memberOf: CN=centosuser,DC=Ezeelogin,DC=com
memberOf: CN=Eztest,DC=Ezeelogin,DC=com
uSNChanged: 53325
name: Irin Mathew
objectGUID:: /FxMlRFpP02h3MkM572bdg==
userAccountControl: 66048
badPwdCount: 0
codePage: 0
countryCode: 0
badPasswordTime: 0
lastLogoff: 0
lastLogon: 0
pwdLastSet: 132593866344903752
primaryGroupID: 513
objectSid:: AQUAAAAAAAUVAAAAxviuHtZf2ydRMK4HVgQAAA==
accountExpires: 9223372036854775807
logonCount: 0
sAMAccountName: irin
sAMAccountType: 805306368
userPrincipalName: [email protected]
objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=Ezeelogin,DC=com
dSCorePropagationData: 20210309201325.0Z
dSCorePropagationData: 20210305030624.0Z
dSCorePropagationData: 20210305025714.0Z
dSCorePropagationData: 16010101000000.0Z
# rini PF., Ezeelogin.com
dn: CN=rini PF.,DC=Ezeelogin,DC=com
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: rini PF.
givenName: rini
initials: PF
distinguishedName: CN=rini PF.,DC=Ezeelogin,DC=com
instanceType: 4
whenCreated: 20210127203733.0Z
whenChanged: 20210309201301.0Z
displayName: rini PF.
uSNCreated: 12754
memberOf: CN=Developers,DC=Ezeelogin,DC=com
memberOf: CN=Eztest,DC=Ezeelogin,DC=com
uSNChanged: 53323
name: rini PF.
objectGUID:: VmjHdiz8qEagbd4Zc9H+2A==
userAccountControl: 512
badPwdCount: 0
codePage: 0
countryCode: 0
badPasswordTime: 132562563956027090
lastLogoff: 0
lastLogon: 132562564935720206
pwdLastSet: 132562564801090925
primaryGroupID: 513
objectSid:: AQUAAAAAAAUVAAAAxviuHtZf2ydRMK4HUAQAAA==
accountExpires: 9223372036854775807
logonCount: 0
sAMAccountName: rini
sAMAccountType: 805306368
userPrincipalName: [email protected]
objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=Ezeelogin,DC=com
dSCorePropagationData: 20210309201301.0Z
dSCorePropagationData: 16010101000000.0Z
lastLogonTimestamp: 132562564935720206
Related Articles
How to use the LDAP password as the security code on user login in SSH?
Can we map existing user group in ldap to Ezeelogin as Ezeelogin user group?
Assigning user group for LDAP users?
How do I configure Ezeelogin to authenticate using OpenLdap or Window AD server?