Authentication of Ezeelogin gateway users using Public keys fetched from Open LDAP server
Integrating SSH Public Key Authentication with OpenLDAP on Ezeelogin
root@ldapserver:~ cat << EOL >~/openssh-lpk.ldif
dn: cn=openssh-lpk,cn=schema,cn=config
objectClass: olcSchemaConfig
cn: openssh-lpk
olcAttributeTypes: ( 1.3.6.1.4.1.24552.500.1.1.1.13 NAME 'sshPublicKey'
DESC 'MANDATORY: OpenSSH Public key'
EQUALITY octetStringMatch
SYNTAX 1.3.6.1.4.1.1466.115.121.1.40 )
olcObjectClasses: ( 1.3.6.1.4.1.24552.500.1.1.2.0 NAME 'ldapPublicKey' SUP top AUXILIARY
DESC 'MANDATORY: OpenSSH LPK objectclass'
MAY ( sshPublicKey $ uid )
)
EOL
Step 2. You need to run the following command to add ldif :
root@ldapserver:~ldapadd -Y EXTERNAL -H ldapi:/// -f ~/openssh-lpk.ldif
Step 3. Login to the GUI of your ldap server. Create a user with the “Generic: User Account” template. Select the user "jake" as shown below
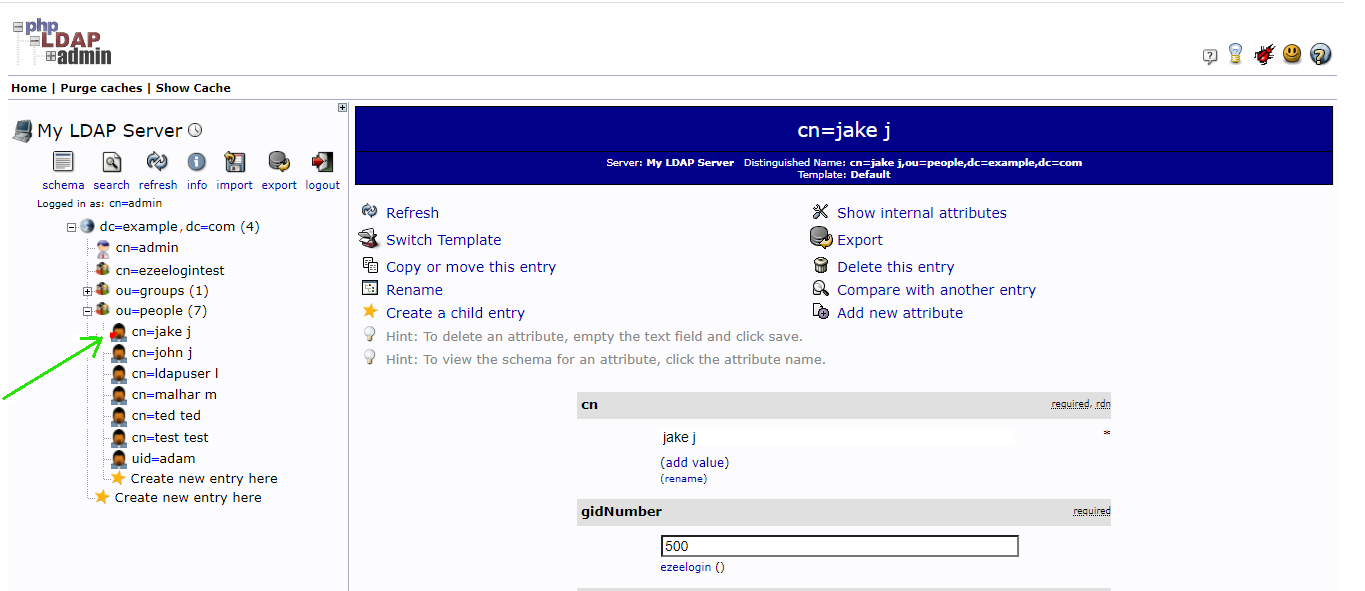
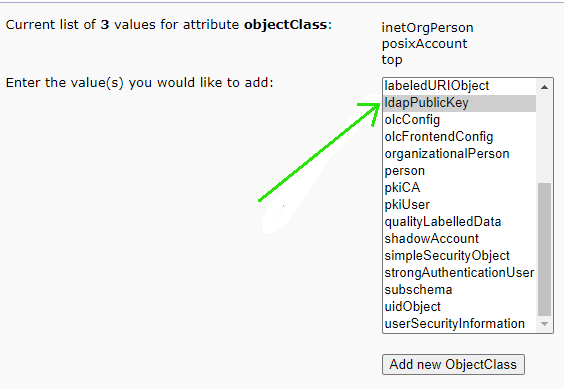
Step 4. Go to the “objectClass” attribute section, click “add value”, and choose the “ldapPublicKey” attribute.

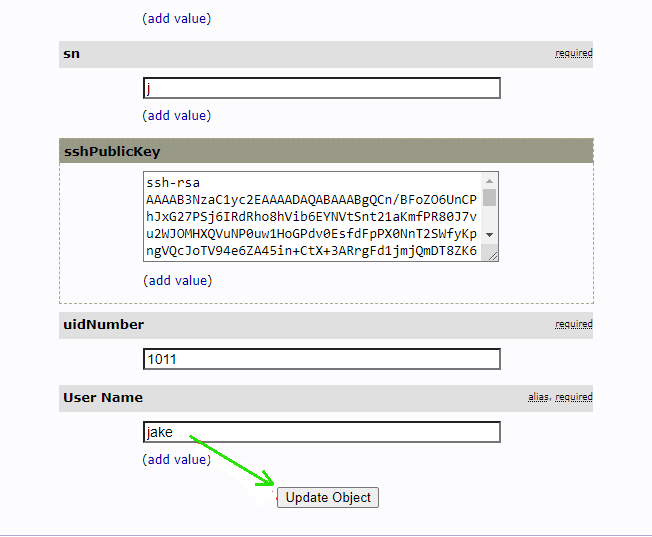
Step 5. After you submit, go back to the user edit page, click “Add new attribute” on the top part, and choose “sshPublicKey”, paste the public key into the text area, and finally click “Update Object”."
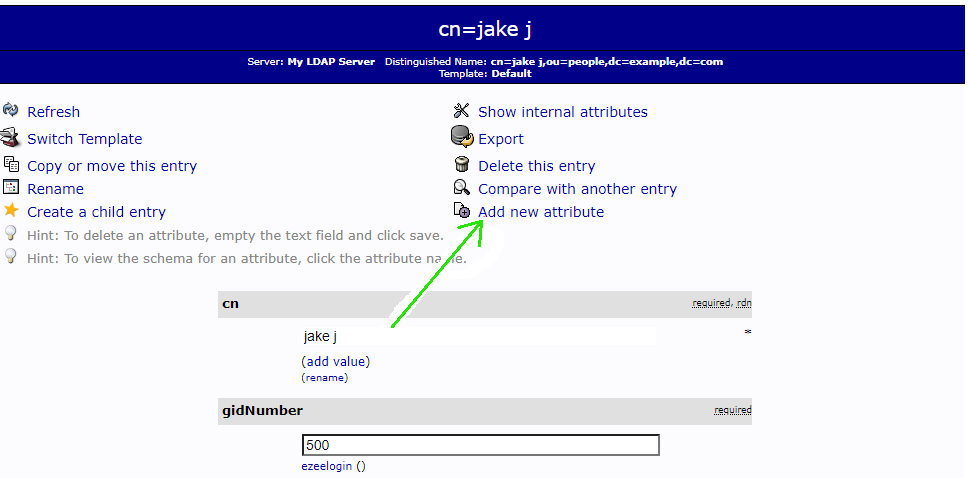
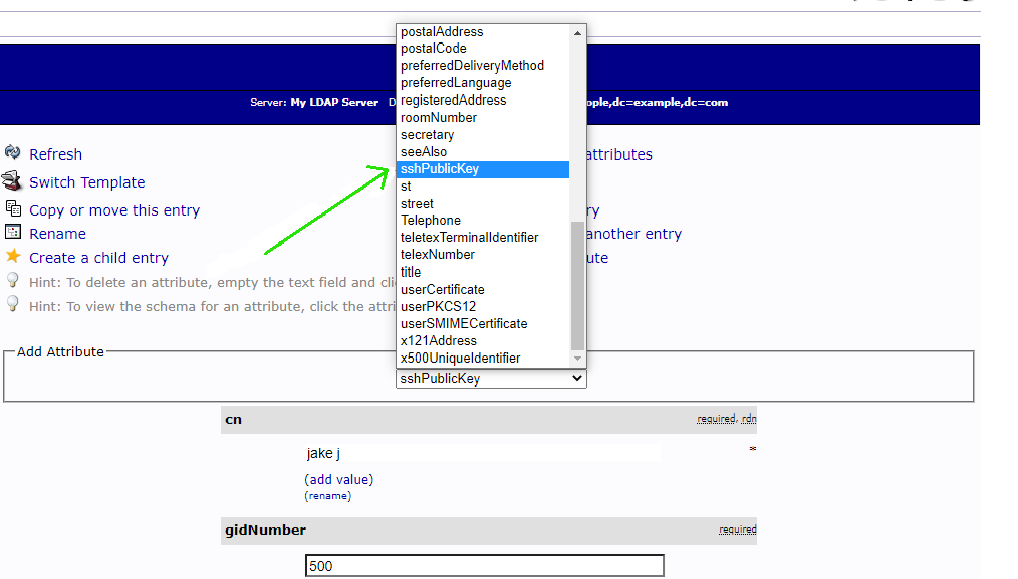
Step 6. Create a script on your Ezeelogin server that queries LDAP for a user's public key under /usr/local/fetchsshkeys
Ensure that the public key is fetched for the user jake from the Openldap server by running the following command
root@jumpserver:~ ldapsearch -x '(&(objectClass=ldapPublicKey)(uid='"jake j"'))' 'sshPublicKey' | sed -n '/^ /{H;d};/sshPublicKey:/x;$g;s/\n *//g;s/sshPublicKey: //gp'
Note: Install the script on your system and make it executable by running: chmod 0500 /usr/local/fetchsshkeys
Step 7. Make sure your /etc/ldap/ldap.conf or /etc/openldap/ldap.conf file is configured to point to the right Open LDAP server For example:
Step 8. Add the following lines on the gateway server to your sshd_config file to point to the script
Related Articles
Can we map existing user group in ldap to ezeelogin as ezeelogin user group ?
Assigning user group for LDAP users?
How to use the LDAP password as the security code on user login in SSH?