How to configure Ezeelogin to authenticate using Open_Ldap(Pam-Ldap) in Ubuntu?
Integration of Open-LDAP (PAM-LDAP) in Ubuntu
Overview: This article describes the process of integrating Open-LDAP (PAM-LDAP) with Ubuntu, including PHP-LDAP installation, Ezeelogin configuration, and PAM-LDAP setup for SSH authentication.
Note: Make sure that the PHP-LDAP extension is installed on the server. Replace the PHP version in the below command.
root@gateway:~# apt-get install phpx.x-ldap
eg: :~# apt-get install php8.2-ldap
root@gateway:~# systemctl restart apache2
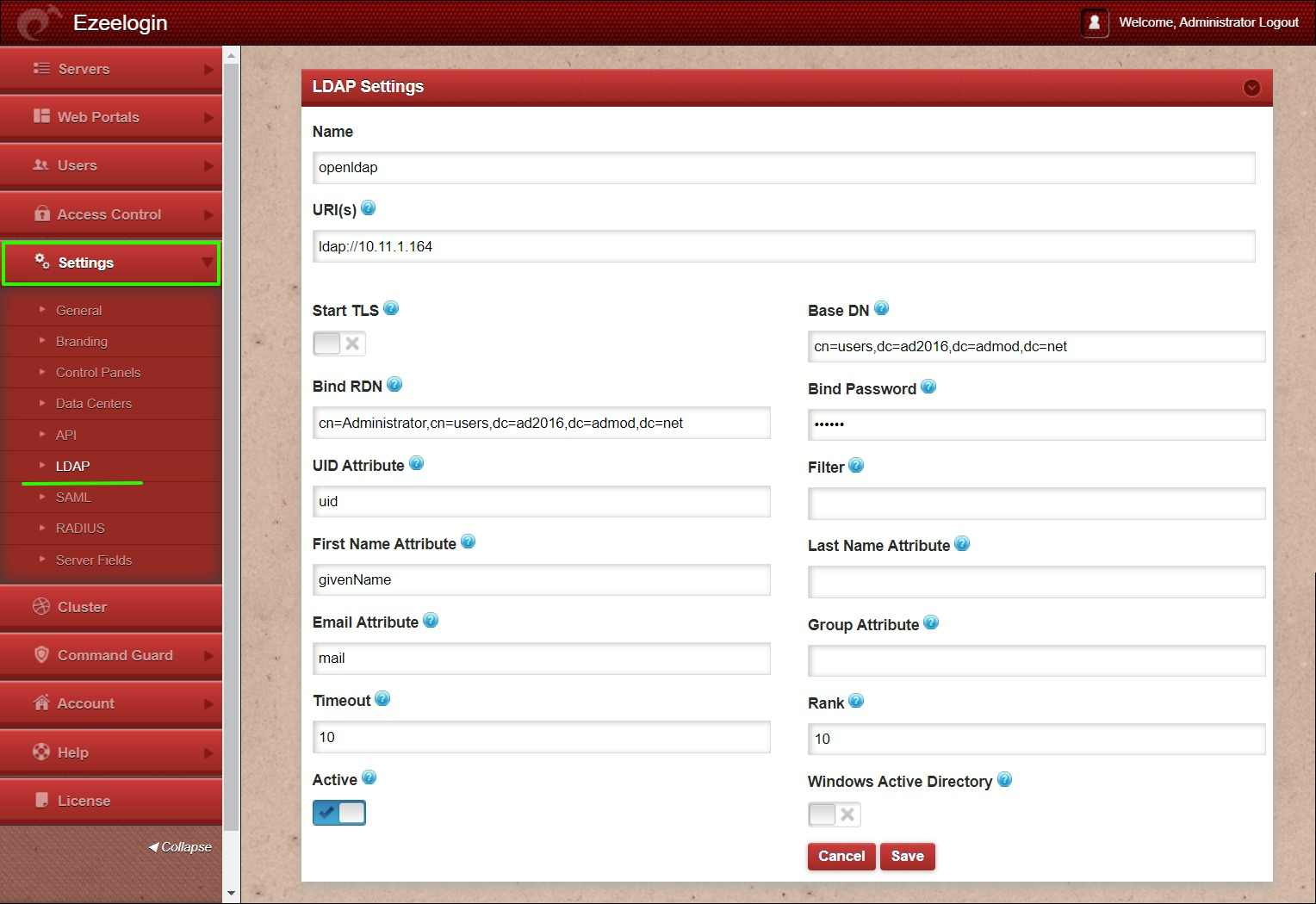
Step 1: Log in to Web-GUI -> open settings -> Ldap and add the details of LDAP configurations.
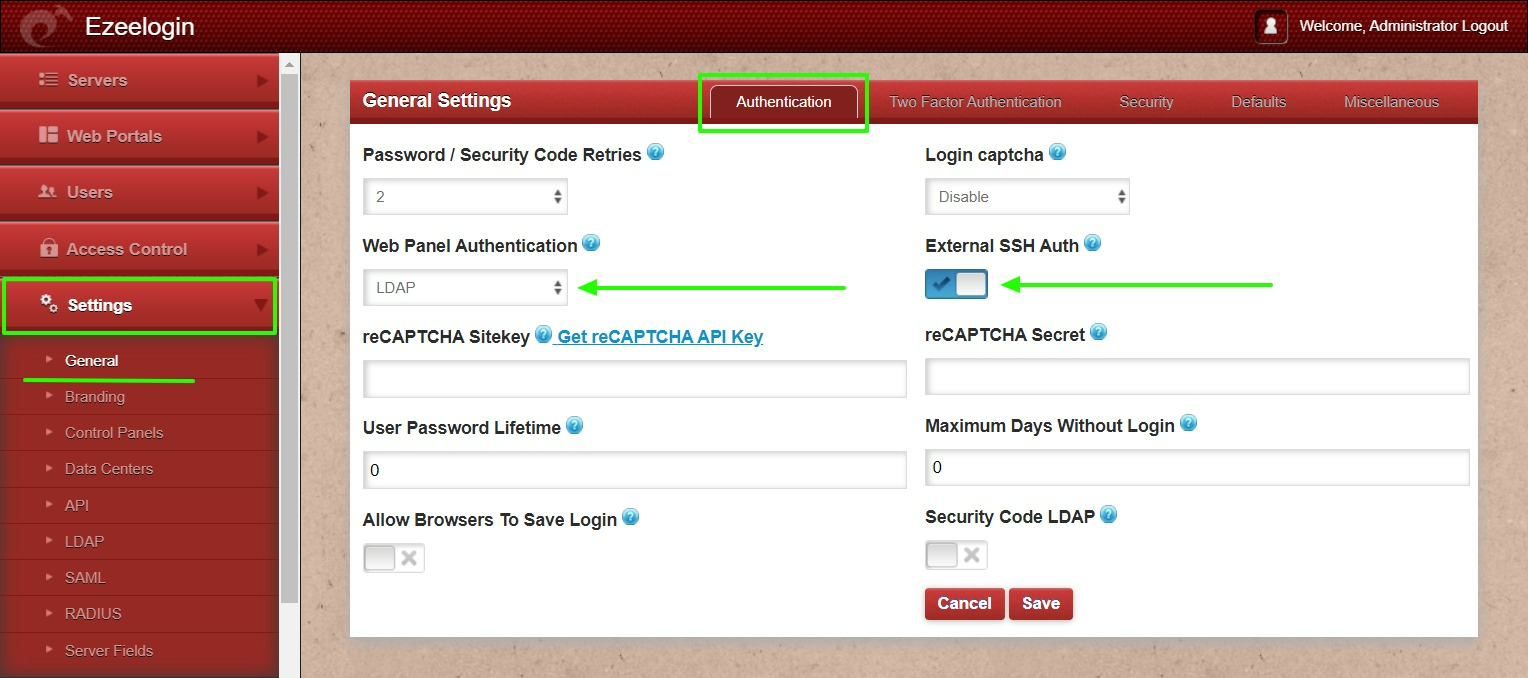
Step 2: Under Settings -> General Settings -> Authentication -> change Webpanel authentication to LDAP & enable External SSH Auth.
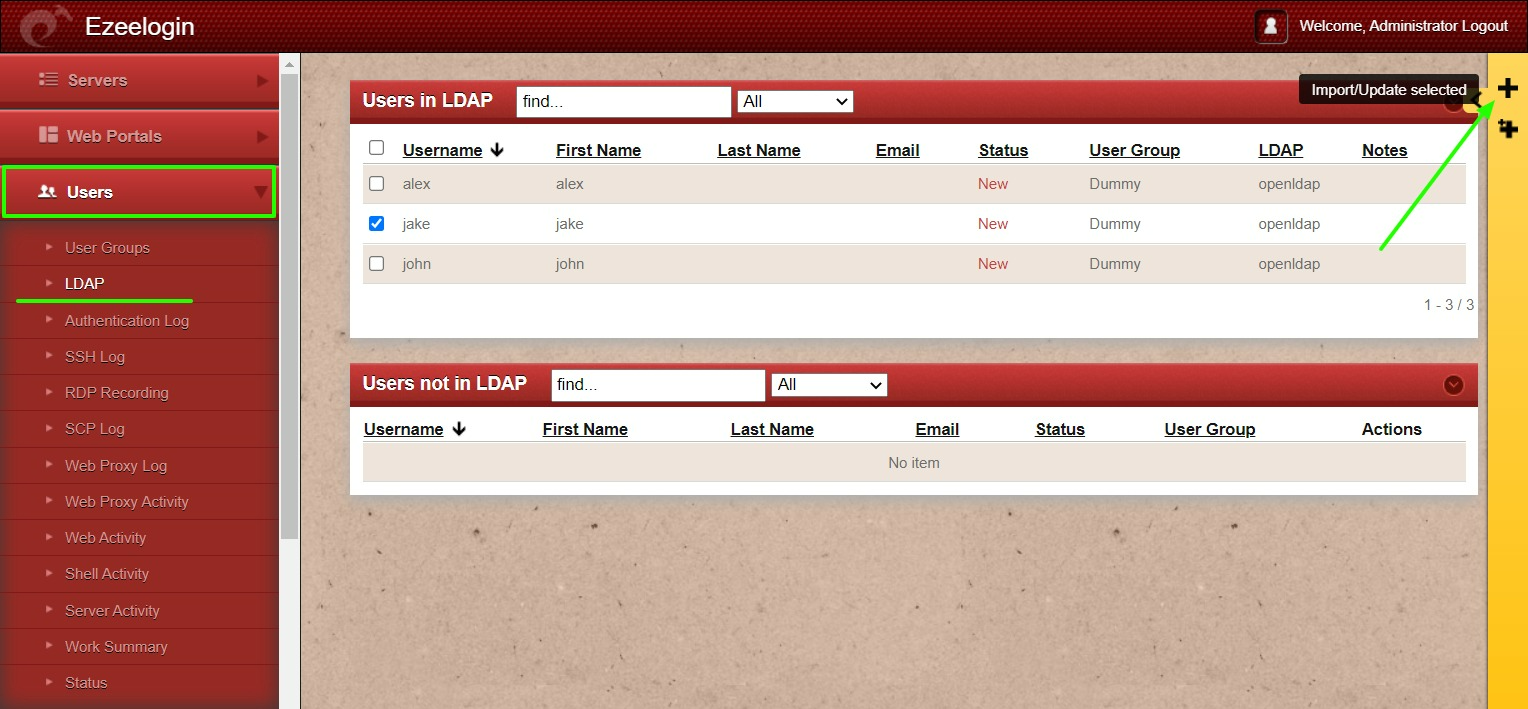
Step 3: Select the LDAP users and import them to ezeelogin.
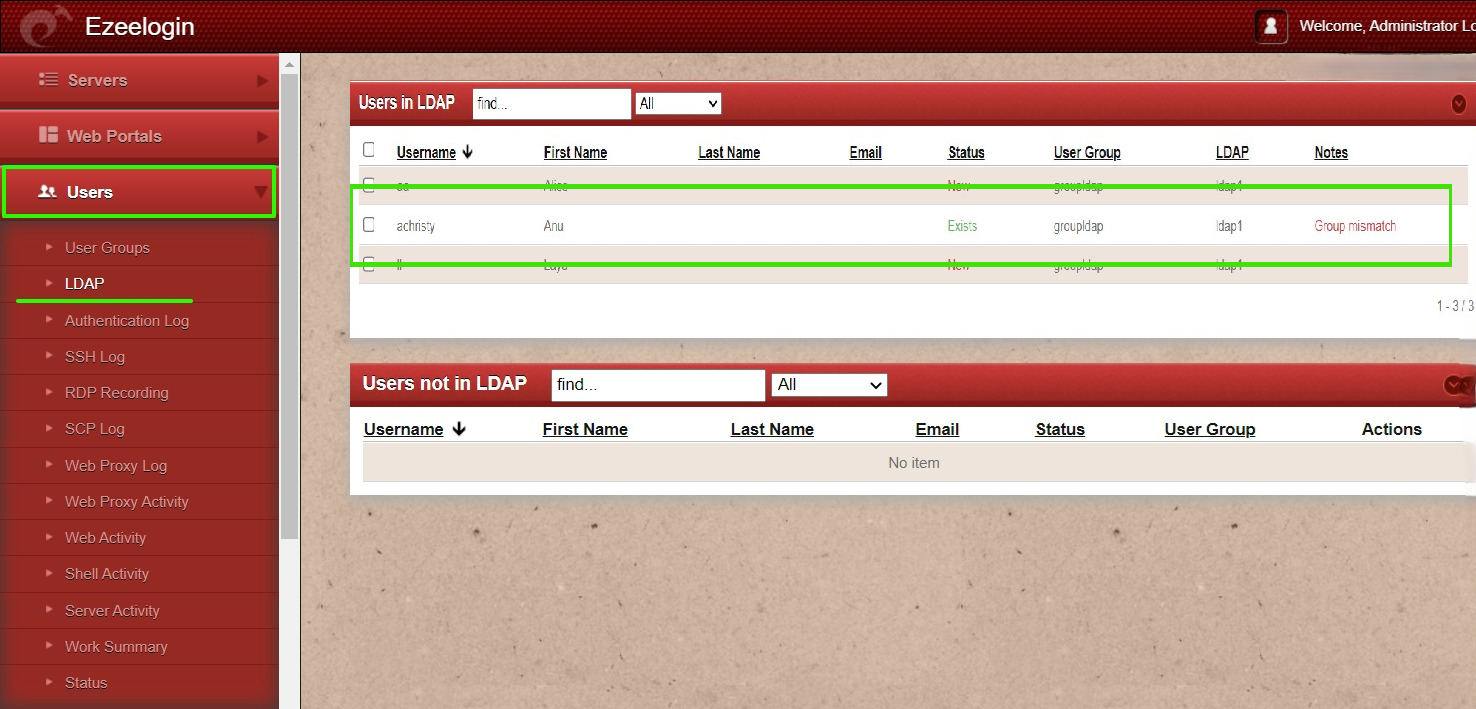
Step 4: You can confirm the imported LDAP users were listed in Users. Now you can login to ezeelogin with ldap user in ezeelogin GUI.
Note: When importing an LDAP user, they will be assigned to the default group or the mapped user group. After the import, if we change the LDAP user to another user group, we will receive a note saying "Group Mismatch." This is not an error.
Note: After importing the users to Ezeelogin, log in with the user and set up security code for the user under Account -> Password -> New Security Code.
Let's configure PAM_LDAP Authentication for SSH
Login to Ezeelogin ssh server to configure pam-LDAP
Step 1: Install pam-LDAP module by the following command
Step 2: Enter LDAP URI, Base DN & select LDAP version 3.
Enter the details in the LDAP setting.
Step 3: Add Binddn & bind password to /etc/ldap.conf
Note: In Ubuntu 16.x, link the directory /etc/openldap with /etc/ldap as follows
root@gateway:~# ln -s /etc/ldap /etc/openldap
Step 4: Append 'ldap' to password,group & shadow in /etc/nsswitch.conf
root@gateway:~# cat /etc/nsswitch.conf
# /etc/nsswitch.conf
#
# Example configuration of GNU Name Service Switch functionality.
# If you have the `glibc-doc-reference' and `info' packages installed, try:
# `info libc "Name Service Switch"' for information about this file.
passwd: compat ldap
group: compat ldap
shadow: compat ldap
hosts: files mdns4_minimal [NOTFOUND=return] dns
networks: files
protocols: db files
services: db files
ethers: db files
rpc: db files
netgroup: nis
Step 5: Enable autocreate home directory on login by adding the following to /etc/pam.d/common-session by the following command
Step 6: Restart nscd service
Note: Ensure the login shell of ldap user is /usr/local/bin/ezsh
Step 7: Now run the id/finger command and see whether you are able to get LDAP user details
root@gateway:~# finger jake
Login: jake Name: franc t
Directory: /home/jake Shell: /usr/local/bin/ezsh
Last login Wed Jun 13 05:02 (EDT) on pts/1 from 10.1.1.13
No mail.
No Plan.
[root@jumpserver ~]# id jake
uid=1547601108(franc) gid=1547600513(domain users) groups=1547600513(domain users)
Note: Run an ldapsearch to check the values returned from your AD server as follows. This is used for troubleshooting.
root@gateway:~# ldapsearch -x -LLL -E pr=200/noprompt -h 10.11.1.164 -D "[email protected]" -w admod_2016 -b "cn=jake,cn=users,dc=ad2016,dc=admod,dc=net"
dn: CN=jake,CN=Users,DC=ad2016,DC=admod,DC=net
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: jake
givenName: jake
distinguishedName: CN=jake,CN=Users,DC=ad2016,DC=admod,DC=net
instanceType: 4
whenCreated: 20180703063304.0Z
whenChanged: 20180703063554.0Z
displayName: jake
uSNCreated: 45128
uSNChanged: 45136
name: jake
objectGUID:: ldpkFlnRs0O6irphlTq1AA==
userAccountControl: 512
badPwdCount: 0
codePage: 0
countryCode: 0
badPasswordTime: 0
lastLogoff: 0
lastLogon: 0
pwdLastSet: 131750731848783837
primaryGroupID: 513
objectSid:: AQUAAAAAAAUVAAAAmhs/bgMv2mlWATm4VQQAAA==
accountExpires: 9223372036854775807
logonCount: 0
sAMAccountName: jake
sAMAccountType: 805306368
userPrincipalName: [email protected]
objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=ad2016,DC=admod,DC=net
dSCorePropagationData: 16010101000000.0Z
uidNumber: 10001
gidNumber: 12000
unixHomeDirectory: /home/jake
loginShell: /usr/local/bin/ezsh
pagedresults: cookie=
How do I configure Ezeelogin to authenticate using OpenLdap(Pam-Ldap) in CentOS
Can we map the existing user group in LDAP to ezeelogin as the ezeelogin user group?