Prevent passwords from being recorded when ssh session recording is enabled
Securing SSH session recording to prevent password capture
Overview: This article describes how to configure SSH session recording to prevent password capture by setting it to "Output" mode in Ezeelogin, crucial for meeting PCI DSS, HIPPA, SOC, SOC2, FFIEC, NERC, NIST, CIP, and ISO 27001 security compliance.
In environments where SSH session recording is implemented for compliance and security reasons, it's crucial to configure it correctly to avoid capturing sensitive information like passwords. This guide walks you through the steps to ensure that only necessary session outputs are recorded, adhering to stringent security standards.
To ensure that passwords are not recorded when the SSH session recording feature is enabled on the SSH gateway server, simply set the "SSH session recording" to Output only which means only STDOUT is recorded. This would record only what is displayed on the user's screen or terminal which is the STDOUT, so the user input when he runs a command on the SSH session and the output of the command executed is recorded.
1. Follow the below steps to choose the ssh session recording mode:
Step 1(A): Log in to web GUI -> Settings -> General -> Security -> Locate SSH session logging -> Select Output mode -> Save it.
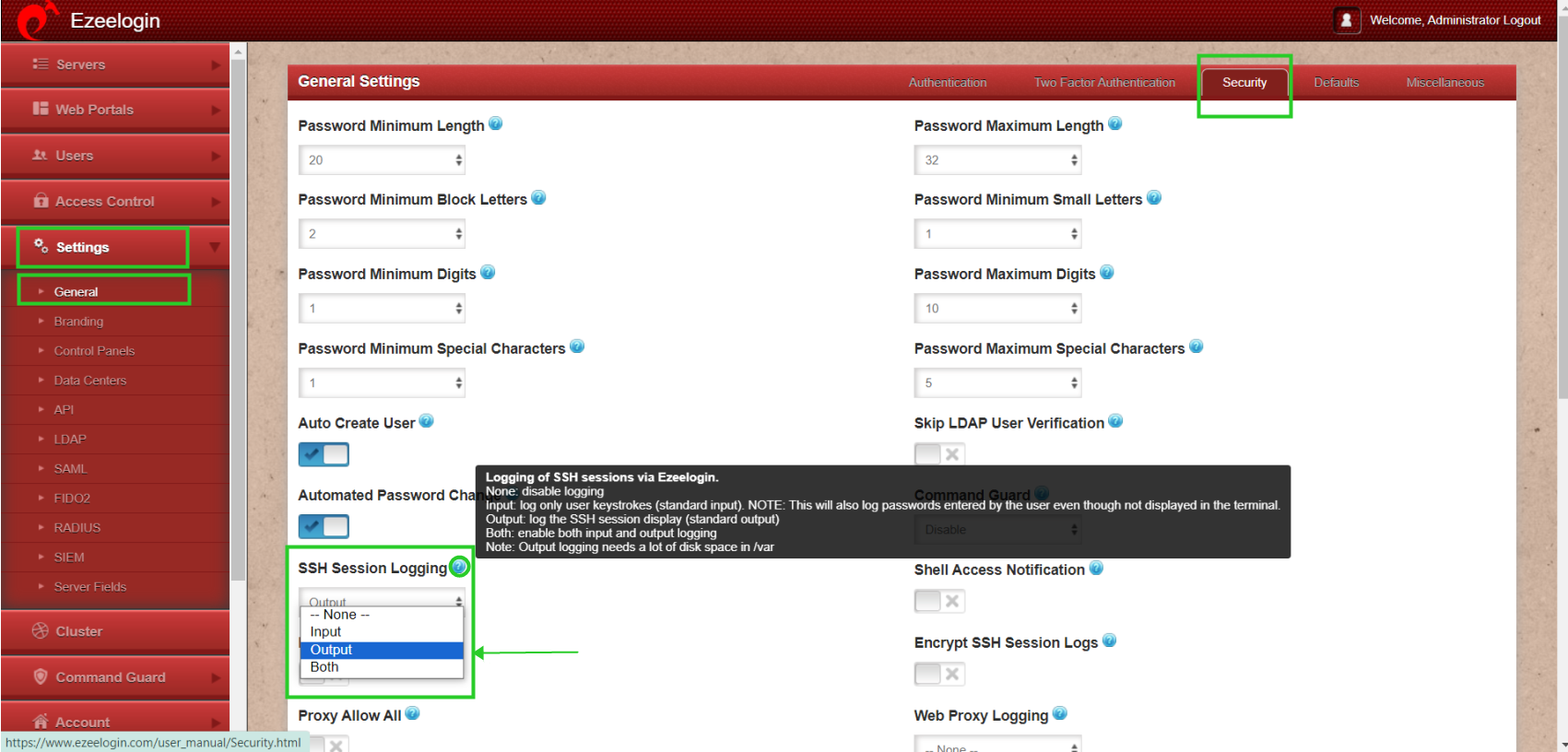
- Output - Refer to the STDOUT file descriptor in Linux. In this mode, what you see on your screen is recorded.
- Input - Refers to the STDIN file descriptor in Linux. In this mode, only what you type on the keyboard is recorded, hence when you set a password that is not visible on your monitor gets recorded. Avoid this mode of recording if you DO NOT want the passwords to be recorded.
- Both - In this mode, both, the STDIN and STDOUT are recorded.
Related Articles: