Configure Ezeelogin to authenticate using Windows_AD / OpenLDAP in Debian?
Configure Ezeelogin to authenticate using Windows_AD / OpenLDAP (Pam-Ldap) in Debian.
Overview: This article describes the steps to configure Ezeelogin to authenticate using Windows Active Directory or OpenLDAP (PAM-LDAP) on Debian, including installing necessary PHP and PAM-LDAP modules, adjusting configuration files, and validating the setup.
Note: Make sure that the PHP-LDAP extension is installed on the server. Replace the PHP version in the below command.
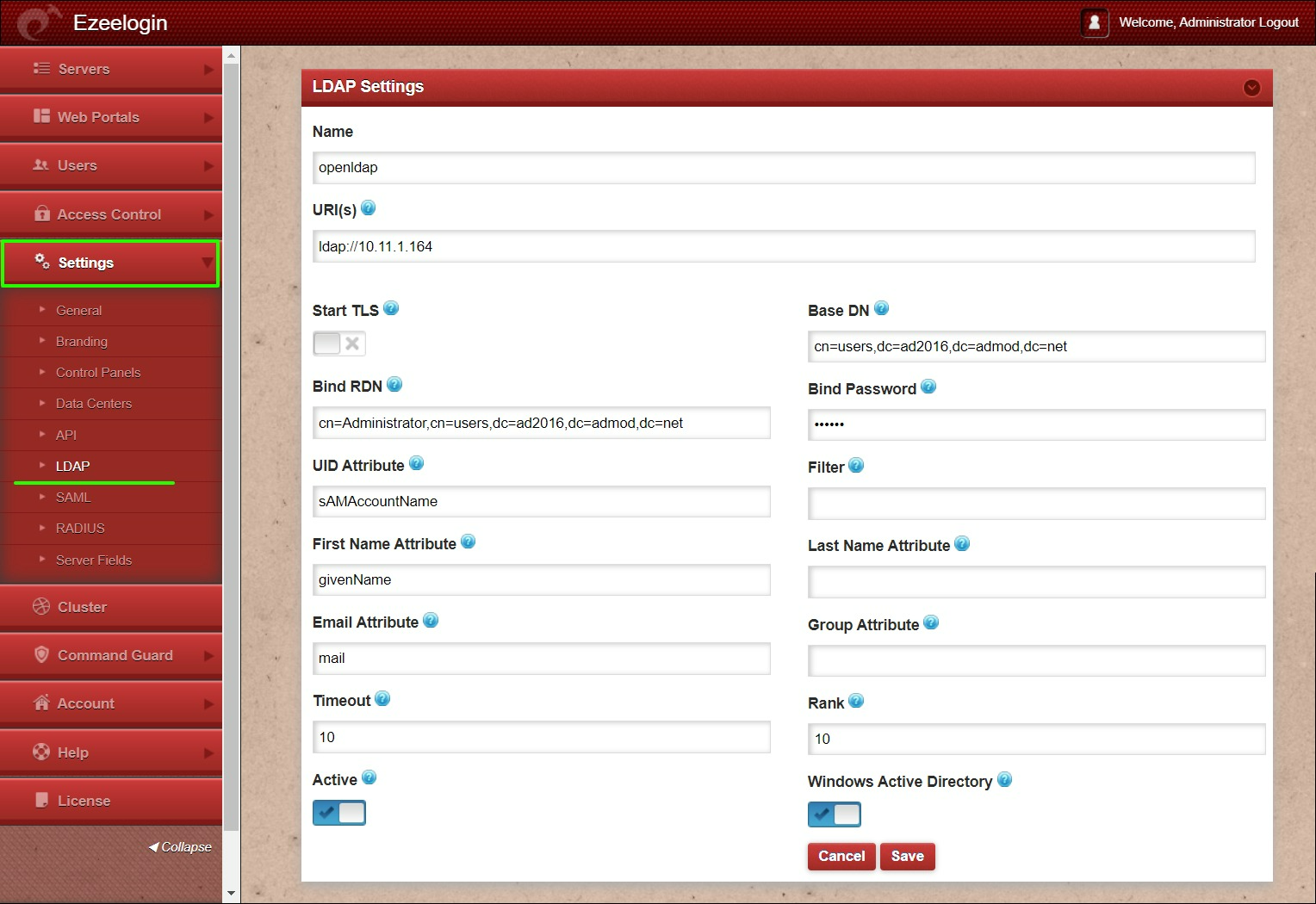
1. Login to Web-GUI > open settings > Ldap
 Add the details of LDAP configurations & Check WINDOWS ACTIVE DIRECTORY if you are authenticating with Windows AD & Save.
Add the details of LDAP configurations & Check WINDOWS ACTIVE DIRECTORY if you are authenticating with Windows AD & Save.
Multiple URIs or a list of URIs can be specified in the format:
- ldaps://host.com:636/ ldaps://host.com:636/
(Only the protocol, hostname, and port fields are allowed.)
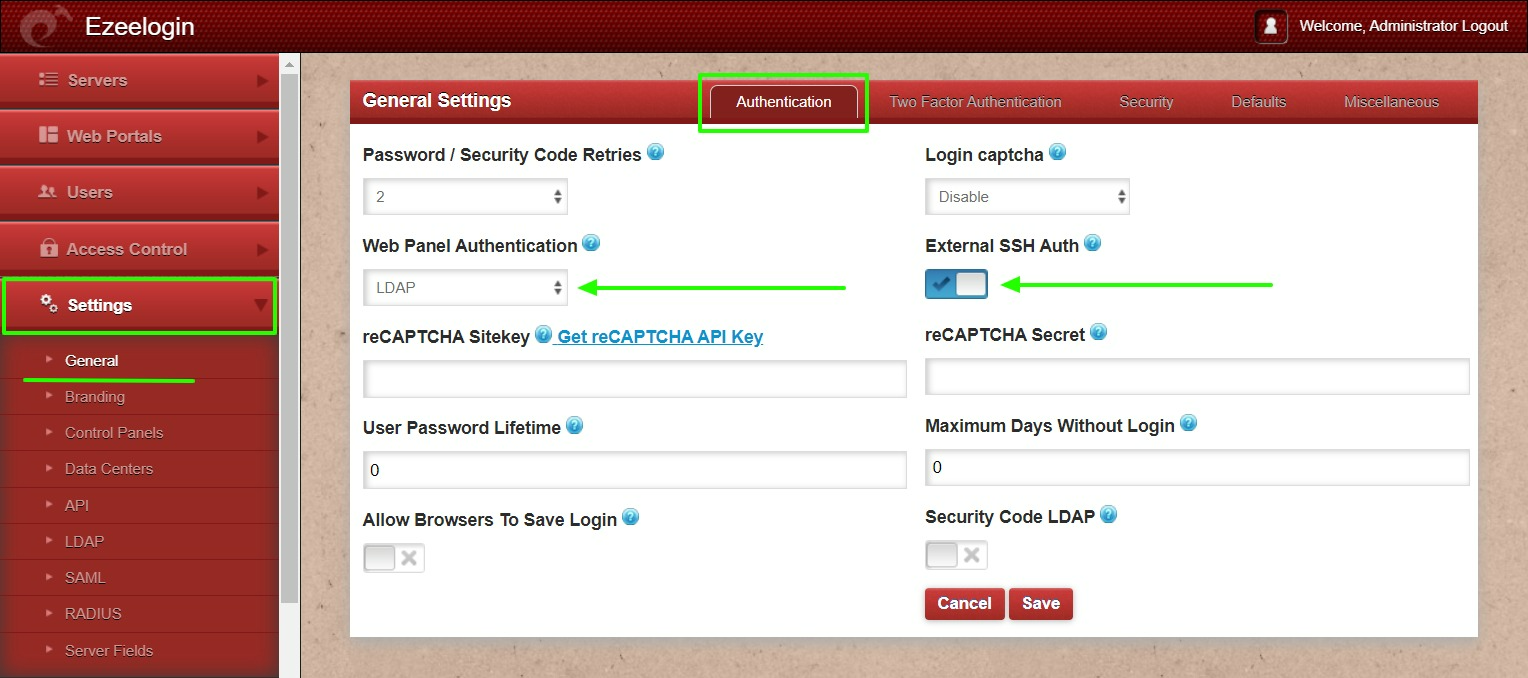
2. Open Settings > General > Authentication > change web panel authentication to LDAP & Check External SSH Auth.
3. Select the LDAP users and import them to Ezeelogin.
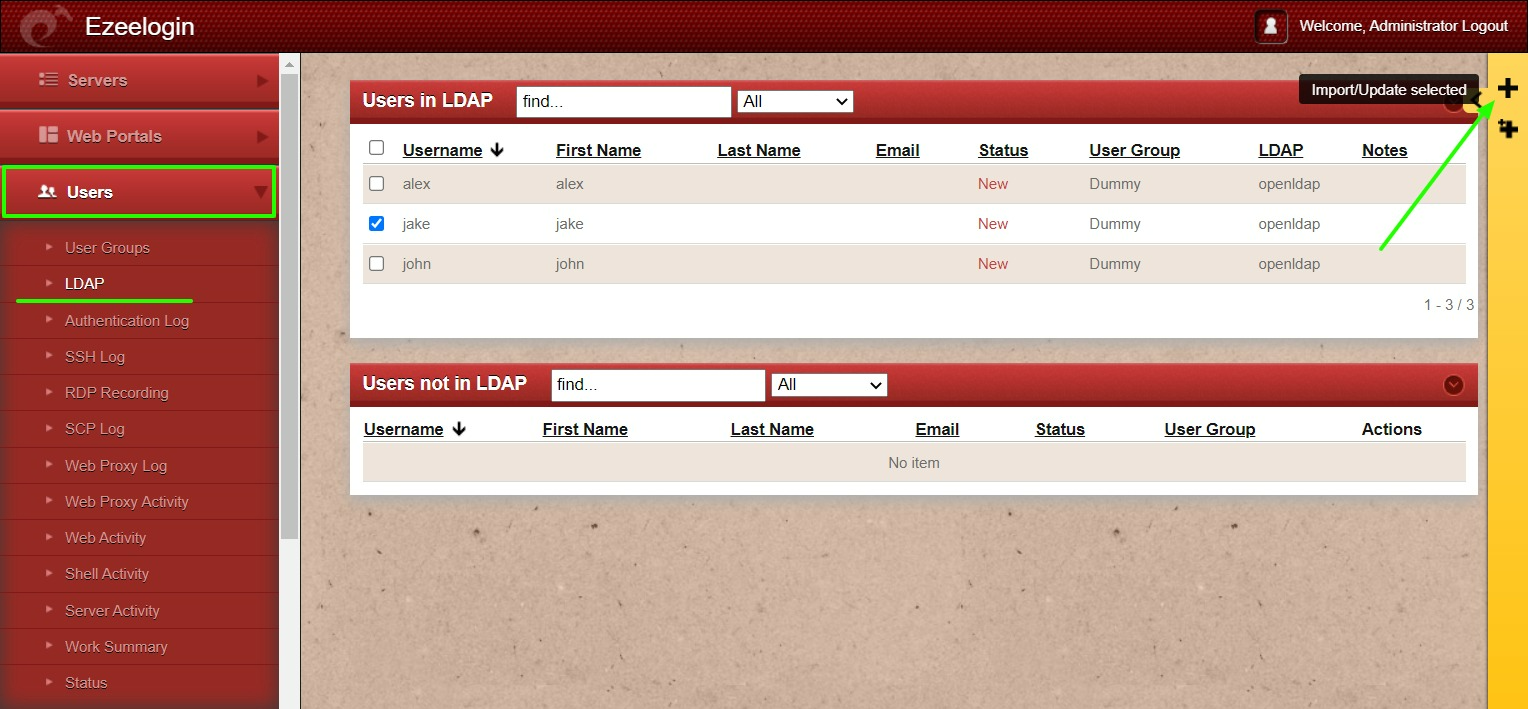
- You can confirm the imported LDAP users were listed in Users.
- Now you can log in to Ezeelogin with LDAP users in Ezeelogin GUI.
- After importing the users to Ezeelogin, log in with the user and set up the security code for the user under Account > Password > New Security Code.
- Skip the 4th & 5th steps if you are configuring OpenLDAP.
4. Make sure that UNIX ATTRIBUTES is enabled on WINDOWS(2003,2008,2012) SERVER.
Note: You do not need to install unix attributes on Windows 10 and Windows 2016 server OS.
- Log in to the Windows server & open the command prompt.
- Enter the below command:
- Reboot the server to complete the installation
5. Make sure to add the values for UID, GID, Login Shell, and Home Directory.
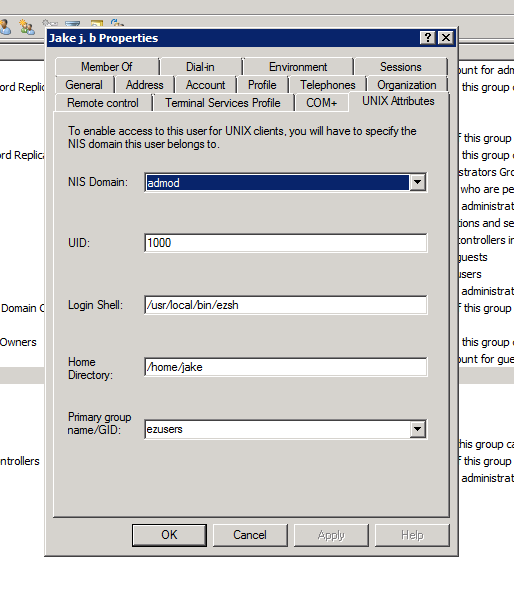
- For Window 2016 AD user set the attributes such as uidNumber = 10001 , gidNumber = 12001 , unixHomeDirectory = /home/jake , loginShell=/usr/local/bin/ezsh
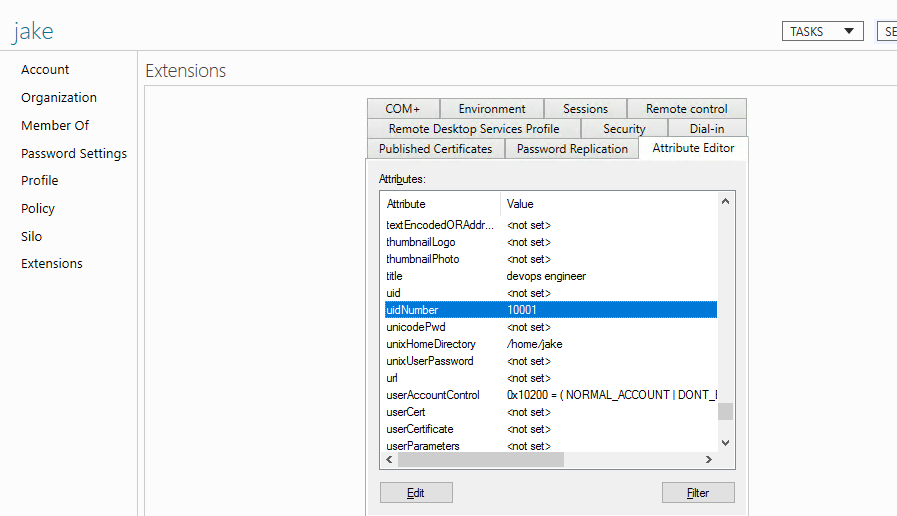
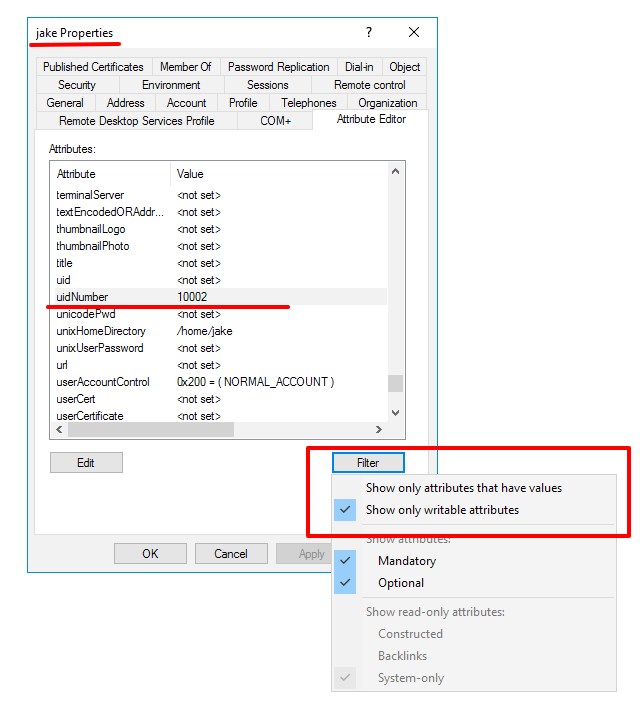
For the Unix Attributes uidNumber, gidNumber, and loginShell to be visible, make sure to click on the Filter button and select ONLY " Show Only Writable Attributes" as shown below.
Let's configure PAM_LDAP Authentication for SSH
- Login to Ezeelogin SSH server to configure pam-LDAP.
- You can reconfigure the settings with the following command
root@jumpserver:~# dpkg-reconfigure libnss-ldap
Note: Skip the 3rd step if you are configuring OpenLDAP.
- Search for RF 2307 (AD) mapping & add or uncomment the following lines.
Note: Ensure the login shell of the LDAP user is /usr/local/bin/ezsh
- Now run the id/finger command and see whether you are able to get AD user details
Note: Run an LDAP search to check the values returned from your AD server as follows. This is used for troubleshooting. Ensure that it returns the values of uid, gid, home directory, and login shell.
Related Articles:
Record and download RDP recordings.
Map existing user group in ldap to Ezeelogin as Ezeelogin user group