SSH Key-based Authentication on Linux Servers
Secure Shell or SSH is a network protocol that helps the users, mainly system administrators to securely access the remote computer over an unsecured network. SSH is the current de-facto method of remote server administration. Before SSH, telnet and rlogin were the primary tools for remote administration. SSH was a game-changer in the computing industry. It offered almost impenetrable security through efficient encryption and enabled server administrators to manage their servers remotely with absolute confidence.
A user can SSH to the remote machine using either password authentication or Key-based authentication. Let’s see how the SSH authentication works in linux.
SSH Authentication
The SSH suite consists of two parts SSH server and SSH client.
>> SSH server runs SSHD daemon and listens on port 22 by default. The server accepts connection requests from machines that have an ssh client installed.
>> SSH clients are part of all Unix or Linux distributions. But if you are a windows user, you may need to use ssh clients such as PuTTY for making ssh connections.
The primary condition for anyone to access a remote server through ssh is a user account with shell access on the server.
Password Authentication in SSH
Access the remote server using ssh either using hostname or ip address of the remote server.
ssh user@remote-server
Now, the system will ask you to enter the password of the ssh user. If the password matches, it permits the login. Password authentication is simple and popular. But it creates some administrative headaches for the server administrators. An ideal password should be a long string of letters, numbers, and special characters. To ensure its security, one should change the passwords at regular intervals. Remembering such a cryptic password is practically impossible for our human brain. So the majority use easy-to-remember passwords or keep them in shareable documents. This lackadaisical attitude encourages attackers to access your login information and perform malicious activities on the server. Besides, the requirement to enter the password manually makes task automation quite challenging.
SSH derives its security from three factors, Asymmetric encryption during authentication, session establishing using symmetric encryption, and hashing to ensure data security during transmission. As the name implies, Symmetric encryption uses the same method for encryption and decryption. So if someone gets access to the ssh key, they can decrypt the messages.
SSH KEYs and Asymmetric encryption
What are SSH keys?
- SSH Keys (Secure Shell Keys) are used as an authentication credential to securely access the remote servers using the SSH protocol.
- SSH key authentication works on the principle of asymmetric encryption.
SSH Keys always come in pairs (public-key and private key). - SSH Keys comprise Public and Private keys which can be generated using the ssh-keygen command.
- System uses different keys for encryption and decryption. So even if one gets access to the encryption key, they can not decrypt it.
- System uses different keys for encryption and decryption. So even if one gets access to the encryption key, they can not decrypt it.
How does SSH Key-based authentication work?
The primary requirement for password-less ssh access is a valid private key in the client machine and the public key in the authorized_keys file. All SSH servers have a file named “authorized_keys.” It contains the public key of all ssh clients with whom it had a previous ssh session. If it is your first ssh connection attempt with the server, it will ask for your confirmation for including your public_key in this file.
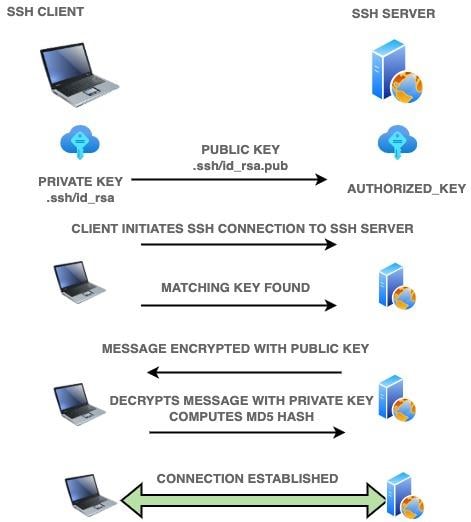
- The client machine shares its public key with the server during the initial handshake.
- The server checks whether the ssh key is present in its authorized_keys file.
- Then the server generates a random number and encrypts it using the client’s public key and challenges the client to decrypt the number.
- The challenge string contains the mutually agreed session-id as well.
- The client decrypts the number using its private key.
- It then generates an MD5 hash using the number and session id.
- When the reply reaches the server, it computes the checksum using the number and session id.
- If the hash values match, a connection is established.
How to configure SSH Key-based authentication on Servers?
~$ ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/home/user/.ssh/id_rsa):
At the following prompt, accept the default or enter the passphrase and press Enter.
Enter the passphrase (empty for no passphrase): passphrase
Enter the same passphrase again: passphrase
Your identification was saved in /home/user/.ssh/id_rsa.
Your public key was saved in /home/user/.ssh/id_rsa.pub.
The key fingerprint is this value:
2. Ensure that the SSH Keys were generated.
:~$ ls -l .ssh/
total 21
-rw------- 1 user user 2655 Mar 30 14:42 id_rsa
-rw-r--r-- 1 user user 578 Mar 30 14:42 id_rsa.pub
3. Enable Key-based authentication on the ssh configuration file by changing “PubkeyAuthentication yes”
vi /etc/ssh/sshd_config
4. Restart the SSH service
5. Add the public key (id_rsa.pub) to remote server’s authorized_keys file /.ssh/authorized_keys. Using the ssh-copy-id command, we can easily add the public key to the remote server.
ssh-copy-id -i id_rsa.pub remore_user@remote_server
6. Disable Password Authentication on the ssh configuration file.
PasswordAuthentication no
Now you should be able to access the remote server by executing the command from your machine.
ssh user@remoteserver
Apart from ssh user access, Cert-based authentication is the default option for VM management in all major cloud platforms such as AWS, Google Cloud, and Azure.
Comparing SSH Keys ( RSA, DSA, ECDSA, and EdDSA )
The encryption algorithm defines the security of each encryption. The most widely adopted encryption algorithms for SSH key generation are RSA, DSA, ECDSA, and EdDSA. Which SSH key is the best? Which type of ssh key should I use? Before that let’s see what’s the difference between these encryption algorithms.
1. RSA (Rivest-Shamir-Adleman)
RSA is the default ssh key type when generated using the ssh-keygen command. It is one of the oldest cryptographic algorithms and is considered the gold standard of asymmetric encryption algorithms. It uses the prime factorization method for encryption. RSA is capable of data encryption, digital signature generation, and verification. RSA is known for its compatibility with all versions of SSH and the robust security it offers. Even though digital signature verification is much faster, RSA is slower for signature generation. The longer ssh keys offer good security, but it significantly reduces the performance.
ssh-keygen
2. DSA (Digital Signal Algorithm)
Digital Signature Algorithm (DSA) ensures each message’s genuineness through a complex hash value. The algorithm requires random, secret, unpredictable, and non-reusable numbers for the signature generation. Even a tiny compromise in these parameters can weaken the security significantly. Hence the quality of the Random Number Generator, RNG, is a defining element for DSA.
ssh-keygen -t dsa
Which is more secure RSA or DSA? Why DSA is weak?
In DSA, signature generation is faster, but verification is slow. It doesn’t offer any data encryption either. For an equal-sized key, both RSA and DSA offer similar security. But the vulnerability incidents are higher for DSA and are not recommended in their original form. OpenSSH 7.0 and higher versions do not support DSA, and it may create compatibility issues.
3. ECDSA
ECDSA (Elliptical curve Digital Signature Algorithm) is an elliptical curve implementation of DSA. The advantage of ECDSA is that it offers similar security as RSA, with almost half of its ssh key size. The small key size significantly improves performance. Since its modified version of DSA, the vulnerability associated with RNG is also present in ECDSA.
All the current SSH clients support ECDSA.
ssh-keygen -t ecdsa
4. EdDSA (Elliptic Curve Digital Signature Algorithm)
EdDSA (Edwards-curve Digital Signature Algorithm) offers exceptionally high levels of data security by generating different signatures for each data. It offers faster signature generation, verification, and batch verification with minimal usage of computational resources. The ssh keys and signatures generated by EdDSA are small and offer security on par with RSA and EcDSA. EdDSA is relatively new and has not yet proven its mettle through vigorous scrutiny like RSA. Similarly, compatibility issues are much higher.
ssh-keygen -t ed25519






