SSH Jump Host
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Introduction
In recent times, there is an increasing need for organizations to give employees access to their IT facilities due to the ongoing Covid restrictions ( such as work from home ) in place and in other cases grant access to external parties like clients, vendors who wants to troubleshoot and fix issues with the IT Infrastructure remotely.
More so, is the need for multiple manage SSH access to the company’s Linux servers, Routers, Switches, while meeting regulatory and security compliance such as PCI DSS, HIPAA, NIST, HITRUST, FedRamp,SOC SOX etc.
This need led to the emergence of the SSH Jump Host concept. It is a secure intermediary server where all your system administrators would login in first via SSH before getting to access the remote devices such as Linux instance, Routers, Switches etc. The purpose of having the SSH Jump host is to improve security and consolidate SSH user activities to a single point hence better security and accountability. SSH Jump Host is also known by the name SSH Jump Box, SSH Jump server, SSH Bastion Host & SSH Gateway.
What is SSH Jump Host?
An SSH Jump Host or ssh jumpserver is a single, hardened server that you ssh through in order to access other servers or devices on the inner network.
Sometimes called an SSH Jump Box, SSH Jump server, SSH bastion host, or a relay host, it’s simply a server that all of your users can log into and use as a relay server to connect to other Linux servers, Routers, Switches and more. Therefore, a jump host is a server inside a secure zone, which can be accessed from a less secure zone. It is then possible to jump from this host to greater security zones.
In other words, it is an intermediary host or an SSH gateway to a remote network, through which a connection can be made to another host in a dissimilar security zone, for example, a demilitarized zone (DMZ). In short, it is intended to breach the gap between two security zones. This is done with the purpose of establishing a gateway to access something inside of the security zone, from the DMZ.
The SSH Jump Host bridges two dissimilar security zones and offers controlled and monitored access between them.
For users accessing your secure network over the internet, the jump host provides a highly secured and monitored environment especially when it spans a private network and a DMZ with servers providing services to users on the internet.
Furthermore, a classic scenario is connecting from your desktop or laptop from inside your company’s internal network, which is highly secured with firewalls to a DMZ. In order to easily manage a server in a DMZ, you may access it via a jump host.
Therefore, a jump host is a server inside a secure zone, which can be accessed from a less secure zone. It is then possible to jump from this host to greater security zones. An example would be a high-security zone inside a corporation. The policy guide states that this zone cannot be accessed directly from a normal user zone. Hence, in a DMZ off the firewall protecting this zone, you have a jump host.
Connections are permitted to the ssh jump host from the user zone, and access to the secure zone is permitted from the jump host. More often, there is a separate authentication method for the jump host fortified with multi factor authentication, Single Sign On ( SSO ) , Radius & more.
How to Set up a SSH Jump Host?
1. Using OpenSSH
A basic ssh jump server with limited features and functionalities can be configured using OpenSSH packages that available by default on most Linux distributions. In the example below, we will just use the basic ssh command line to proxy a ssh connection to the remote server via an intermediate jump server.
ssh -J jump_host_machine remote_machine
If the -J option is not available use the -W option to pivot the connection through an intermediate bastion host.
ssh -o ProxyCommand="ssh -W %h:%p bastion.gateway.org" remote.server.org
With the OpenSSH 7.3, the easiest way to pass through hop through intermediate one or more jump hosts is using the ProxyJump directive ssh_config.
Multiple jump hosts can be chained as well.
Host remote server
HostName 192.168.0.177
ProxyJump admin@jump-server.org:22, admin@jump-server2.org:22
User devops
Do refer to the article SSH Proxy and SSH JumpHost for configuring a basic jump host that is very limited in feature and functionality when compared to the modern-day ssh jump host solutions.
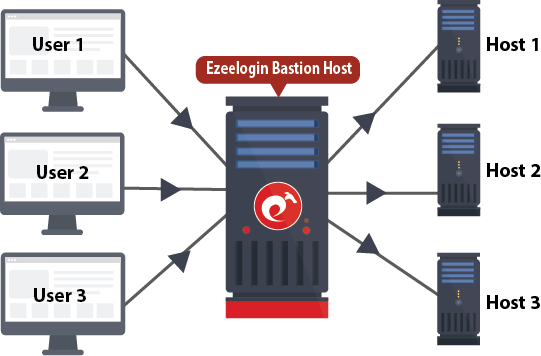
2. Using Ezeelogin
Ezeelogin is a much more powerful and advanced SSH Jump host software solution and can be deployed quickly. It has powerful features that make managing hundreds of Linux devices and granting ssh access to these devices a piece of cake. Do refer to the article to set up and configure an ssh jump host quickly on your premise or on the cloud.
Why do you need a SSH Jump host solution to manage ssh access?
The OpenSSH-based jump host is clearly not enough to meet the modern-day requirements of an IT enterprise. The challenges for the enterprise are constantly changing and dynamic. One day, it could be from maintaining security, granting ssh access to the users to the designated server, and that too for a particular time and on another day it could be the security compliances that need to be met at the time of a Linux servers infrastructure audit.
The modern-day SSH Jump host solutions are designed to address the challenges faced by an IT enterprise when it comes to security and to meet various security compliances like PCI DSS, NIST, ISO 27001, and more.
The modern-day ssh jump host software has the following features and more.
- Identity and Access Management (IAM)
- Privileged Access Management (PAM)
- Role Based Access Control to delegate access to Linux servers and Network devices
- Two-factor authentication methods like Google Authenticator, DUO Security 2FA, & Yubikey in SSH
- Integrates with Windows Active Directory, OpenLDAP, and Redhat IDM
- Supports SAML for Single Sign On
- Support RADIUS Authentication to access network devices such as Routers and Switches
- Password Manager
- SSH key rotation
- Automated root password management
SSH Jump host best practices
To ensure maximum protection of your ssh jump host, you should focus on the process of server security hardening. In simple terms, that means applying a combination of basic and advanced security measures to address vulnerabilities in your bastion host server and operating system to boost overall server security.
Find how to secure your ssh jump host?
CONCLUSION
IT Enterprises that use an SSH Jump Host solution in improving the security of their critical IT asset and in meeting various mandatory security compliances such as PCI DSS, HIPAA, NIST, SOX, SOC, HITRUST (which would otherwise prove very costly in case of a breach), are more likely to succeed due to the improved operational efficiency, digital security, hence more successful business for the company’s end customers.






