Securing Connections: Exploring the Basics of SSH
What is SSH ( Secure Shell)?
SSH (Secure Shell) is a network protocol that many people use to access remote systems safely, even when using an unsecured network. It allows system administrators and developers to log into remote computers and execute commands from afar, making it a pretty important tool. Configuring SSH is paramount, as it ensures security and improves convenience, optimizing the overall SSH experience. This article covers the basics of SSH configuration, including how it works, various configuration options, best practices, and a discussion on how to use SSH jump and bastion hosts to enhance network security.
Why SSH Should Be Your Go-To Choice?
Prior to SSH, Telnet, rlogin and FTP protocols were used for remote access and file transfer. However, they use plain text methods making them vulnerable to security breaches.
Later, SSH became an optimal solution in terms of security to these protocols ensuring the protection of communication and uphold data integrity between client and server. It uses a client-server model to establish a secure communication between two devices or computers.
What is OpenSSH?
OpenSSH stands out as the leading connectivity solution for remote login utilizing the SSH protocol. It eliminates connection hijacking and other attacks by encrypting all the traffic. It was originated as a component of the OpenBSD project, it made its debut in 1999. Initially, it served as a secure alternative to unencrypted protocols like Telnet, rlogin, and FTP. Presently, it is seamlessly integrated into numerous operating systems, including Microsoft Windows, macOS, and Linux.
Some important cli utilities included in OpenSSH are: SSH, scp, sftp, ssh-add, ssh-agent, ssh-keygen, ssh-keyscan.
a) ssh : Remote login client
b) sshd : sshd is the openssh server process, which handles user authentication, encryption, terminal connections, file transfer and tunnelling.
c) scp (Secure file copy) : scp use ssh protocol to securely copy files between servers.
scp pathtosourcefile pathtodestinationfile ( use -r option to copy the entire content of the directory)
d) ssh-add : Tool to add ssh private key to ssh authentication agent for implementing single sign-on.
e) ssh-keygen : Generate ssh key pair for authentication
How does SSH works?
SSH uses the client-server architecture with encryption and authentication mechanisms to create a secure connection over the network. The server is the computer or devices you want to access, and the client is the computer you are using to access it.
The SSH server uses the TCP port 22 (by default) to listen for incoming connection requests and provides authentication to the client by verifying its key. The client uses a TCP handshake to make a connection request. If the credentials are authenticated by both, SSH access is granted, and a secure connection is established between the SSH server and the SSH client.
Let us take a brief look at the entire step-by-step process of SSH connection between the SSH server and SSH client.
1. Connection request – The SSH client initiates the connection request to the SSH server. A TCP handshake request is made by the client for that.
2. Authentication and Encryption between SSH server and client – The SSH server uses a public key which is verified by the SSH client to check the server’s identity. On the other hand, a shared key is generated by the client which is shared with the server to start the data transmission.
3. User authentication – After the establishment of a successful connection, a user needs to authenticate with a username and password.
Encryption Techniques in SSH
1. Symmetric Encryption (Shared Key Encryption) –
Symmetric encryption employs a single key for both encryption and decryption, ensuring mutual agreement on the shared key. The client and server establish this secret key through a negotiated agreement method. Drawback for symmetric encryption would be that both the sender and receiver would need the same key which could be kept always hidden.
2. Asymmetric Encryption :-
In Asymmetric Encryption, public and private keys are used in this technique to encrypt and decrypt data over the network. Most widely used encryption is RSA encryption.
3. Hashing :-
This is a little advanced encryption technique that generates a cryptographic hash value or hash code that cannot be reversed to get the actual data. The job of collecting the data is done by the hash function. It is a one-way hash function. It is impractical to derive the original data from the hash value hence it is used widely in safeguarding password storage, identity verification, etc It does not reveal the password in a data breach. Hence it is an industry standard when it comes to password storing.
How to use SSH?
System administrators use SSH for secure remote access and management of servers and devices. Let’s see how we can use SSH on different operating systems.
Windows:
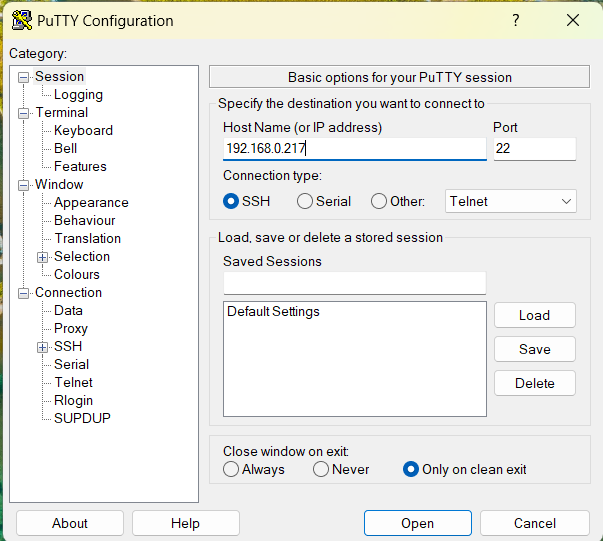
a) Install an SSH Client: If not already installed, download and install an SSH client like PuTTY or Git Bash.
b) Launch the SSH Client: Open PuTTY or Git Bash.
c) Enter Connection Details: Enter the hostname or IP address of the remote server, specify the port (default is 22), and choose SSH as the connection type.
d) Authenticate: If using password authentication, enter your username and password when prompted. If using SSH keys, configure them in your client.
e) Connect: Click “Open” or press Enter to connect to the remote server.
macOS and Linux:
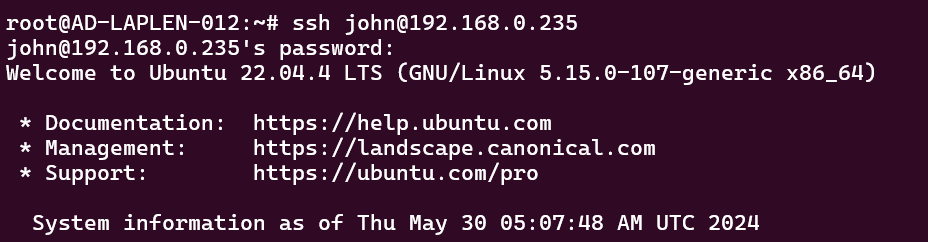
a) Open Terminal: Launch the Terminal application.
b) Enter SSH Command: Type ssh username@remote_server_ip where username is your username on the remote server and remote_server_ip is the IP address or hostname of the server.
c) Authenticate: If using password authentication, enter your password when prompted. If using SSH keys, ensure they are properly configured.
d) Connect: Press Enter to connect to the remote server.
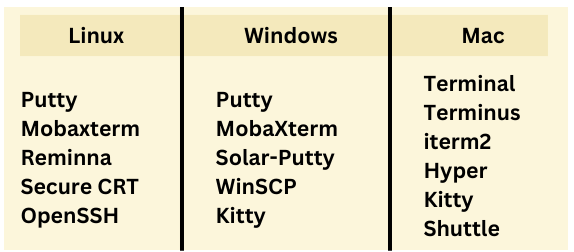
Popular SSH Clients
On What devices you can use SSH?
b. macOS
c. Network devices (routers, switches, firewalls, and Network attached devices.
d. Embedded systems such as IOT devices, electronics, and controllers
e. Virtualization platforms such as VMware vSphere, Microsoft Hyper-V, and KVM (Kernel Virtual Machine)
f. Cloud computing platforms AWS, Microsoft Azure, and Google Cloud Platform
Best Practices for SSH
While using SSH we must ensure the integrity and security of our data during the transmission. Some of the recommended best practices include
1. Strong Passwords or SSH keys
Instead of utilizing simple, weak passwords, use SSH keys or strong complicated passwords for authentication.
2. Disable Password Authentication
Disable password authentication for SSH wherever possible and use SSH keys only for authentication to reduce the risk of brute force attacks.
3. Limit SSH Access
Use tools like SSH keys, IP whitelisting, and VPNs, or configure firewall rules and TCP wrappers to limit SSH access to only approved users and hosts.
4. Strong Encryption Algorithms
Make sure that strong encryption algorithms, like AES, are used for SSH traffic to ensure data integrity and privacy during transmission.
5. Utilize SSH Configuration Options
Preventing root login, limiting the number of open sessions, imposing idle session timeouts, and restricting SSH commands are some SSH configurations to improve security while using SSH.
6. Two-Factor Authentication
To add an extra layer of protection, enable two-factor authentication in addition to their SSH key or password, such as a one-time password (OTP) or biometric authentication.
7. Monitor SSH Logs
Check SSH logs frequently for unauthorized access, failed login attempts, and suspicious activities. To keep track of SSH sessions and identify security issues, implement logging and auditing procedures.
Conclusion
Finally, we can say that SSH is the perfect and evergreen solution to provide secure remote communication between two remote systems. By understanding all its aspects, we can leverage its potential to perform diverse types of tasks on remote systems easily.







